
The AI SRE for complex production environments
Cleric investigates production issues, captures what works, and makes your whole team faster.
5 min
Time to Root Cause
92%
Actionable Findings
200,000+
Production-Grade Investigations
“I see Cleric functioning as an SRE companion for our Software Engineers. If one team has already solved an alert, we can apply that knowledge elsewhere.”

Maxime Fouilleul
Head of Infrastructure & Operations
Meet Cleric
Cleric investigates problems, surfaces answers, and learns from your engineers.
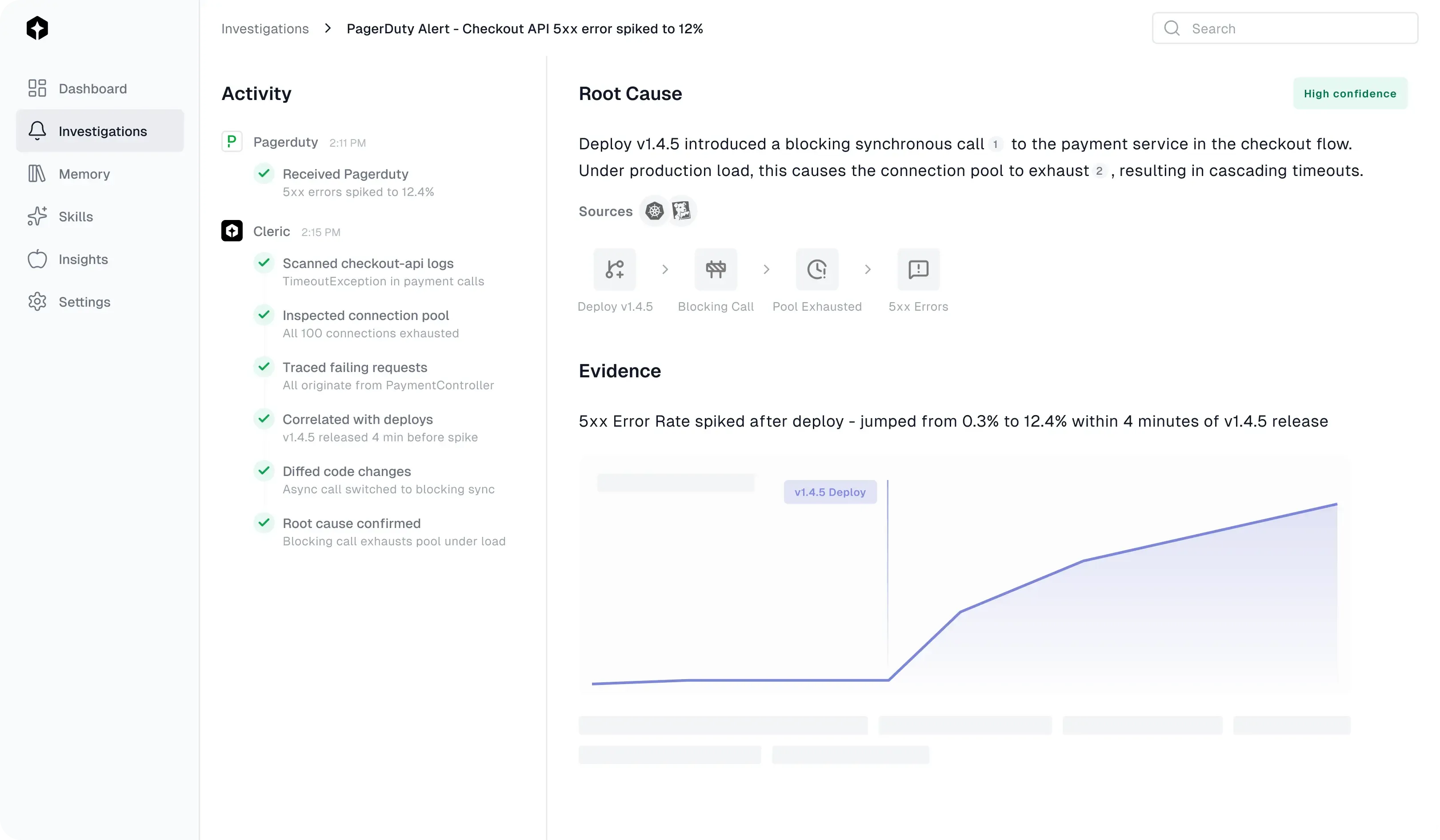
Things break. Cleric investigates.
While you’re still reading the alert, Cleric’s already three steps into the investigation.
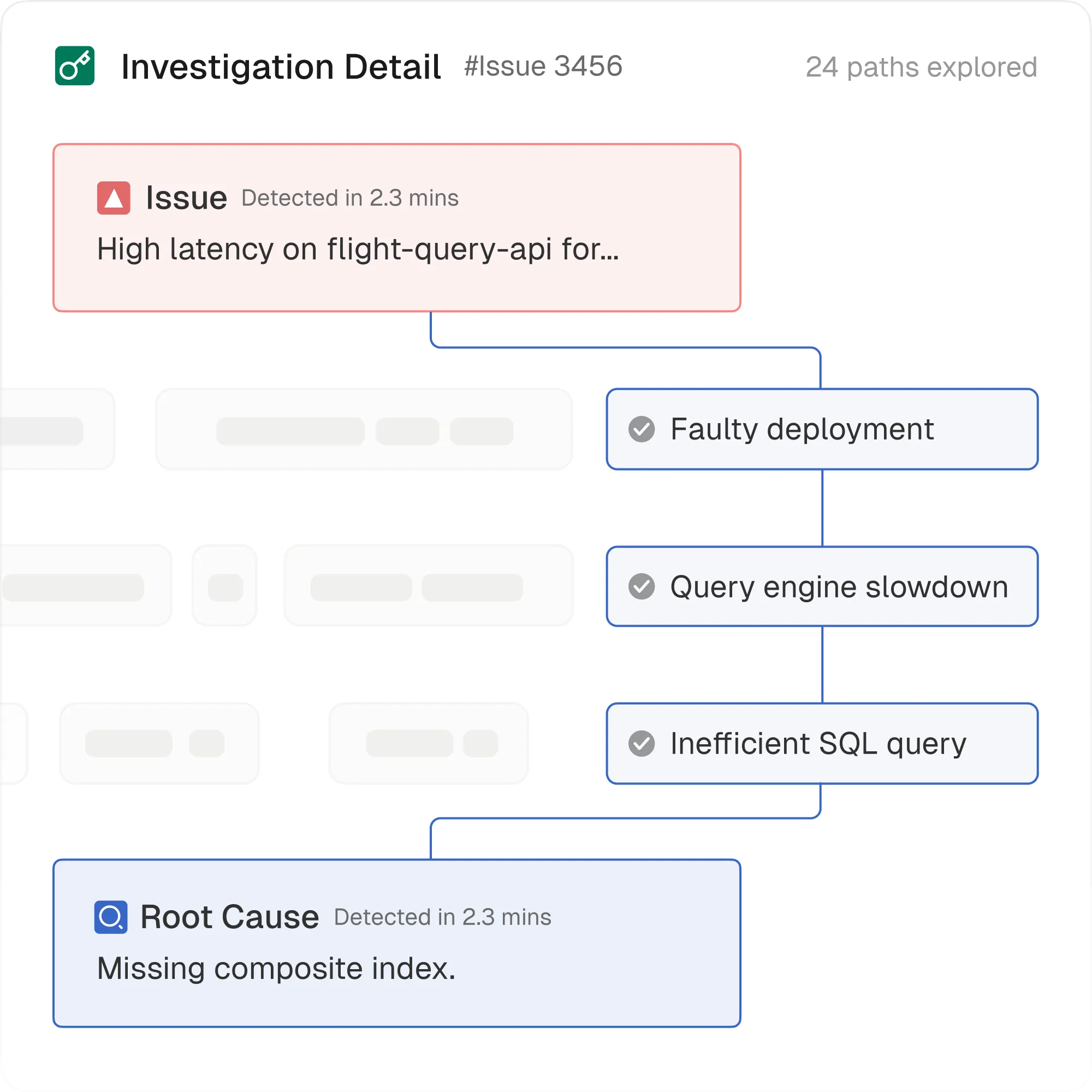
Skip straight to the answer
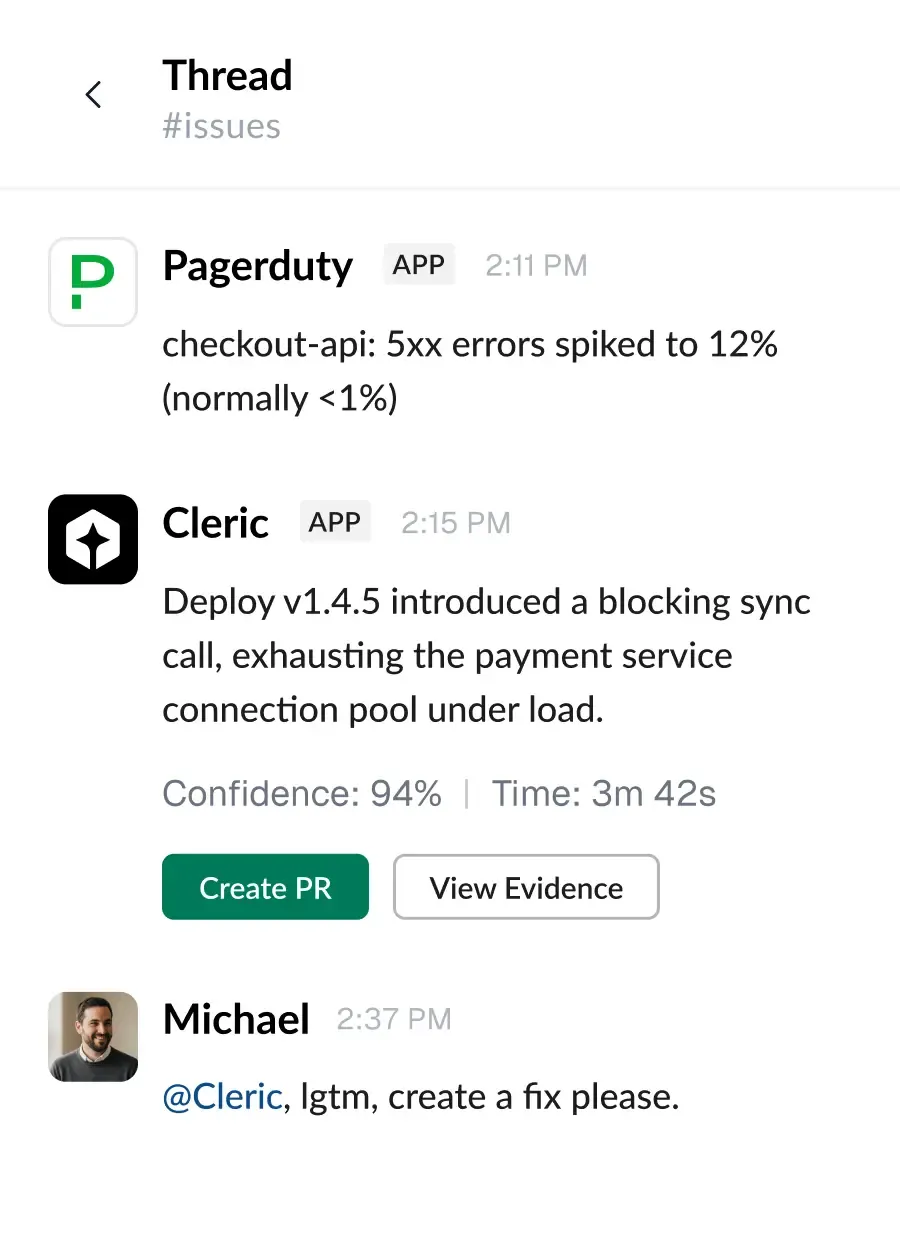
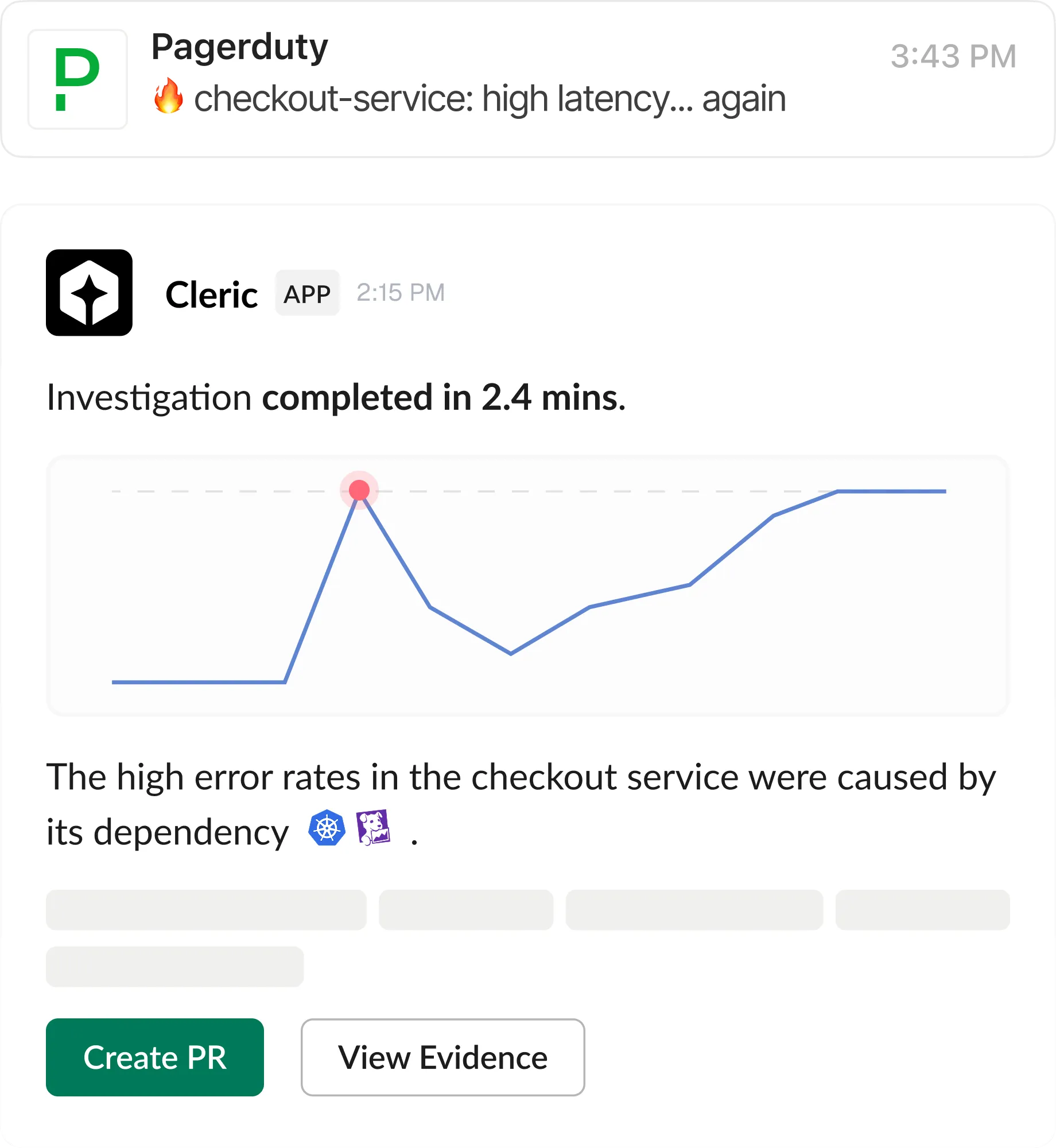
Cleric automatically investigates alerts and delivers root cause analysis so you know exactly what's wrong and whether to act.

Trust but verify
See exactly how Cleric reached its conclusions so you can trust the diagnosis and move to resolution.

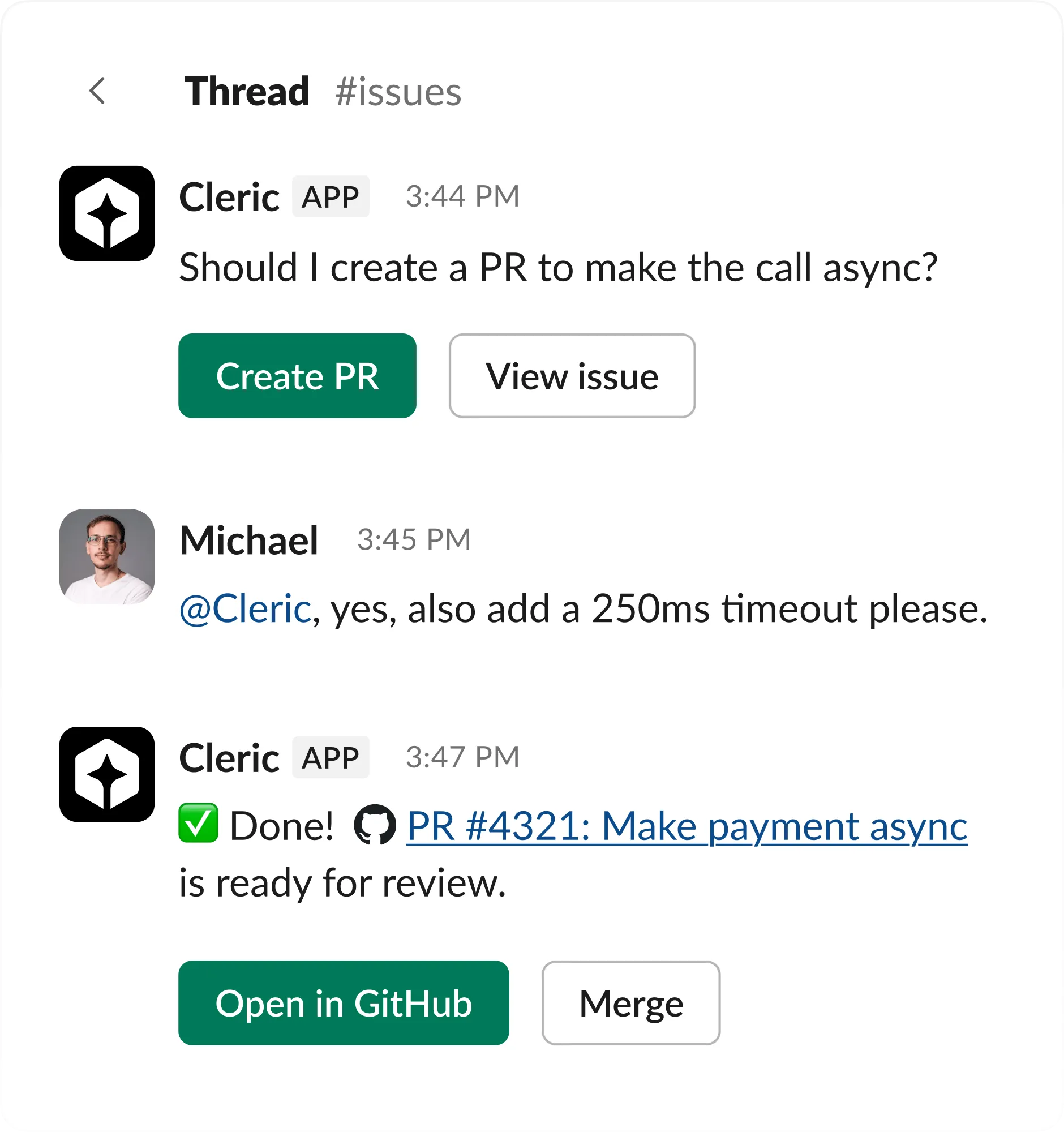
Ship a fix
Work with Cleric to ship fixes by asking questions, giving instructions, and collaborating until the issue is resolved.
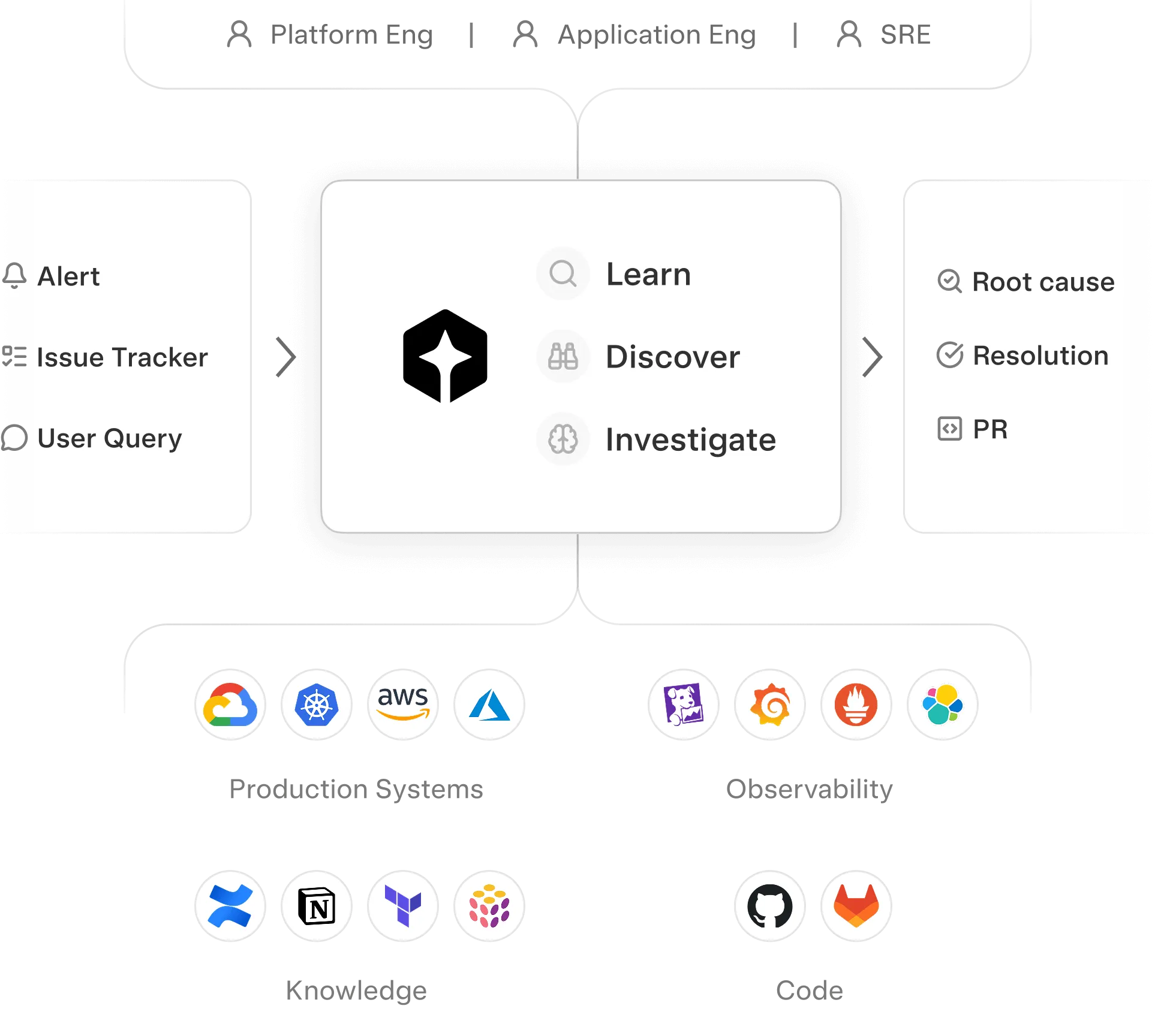
Works inside your

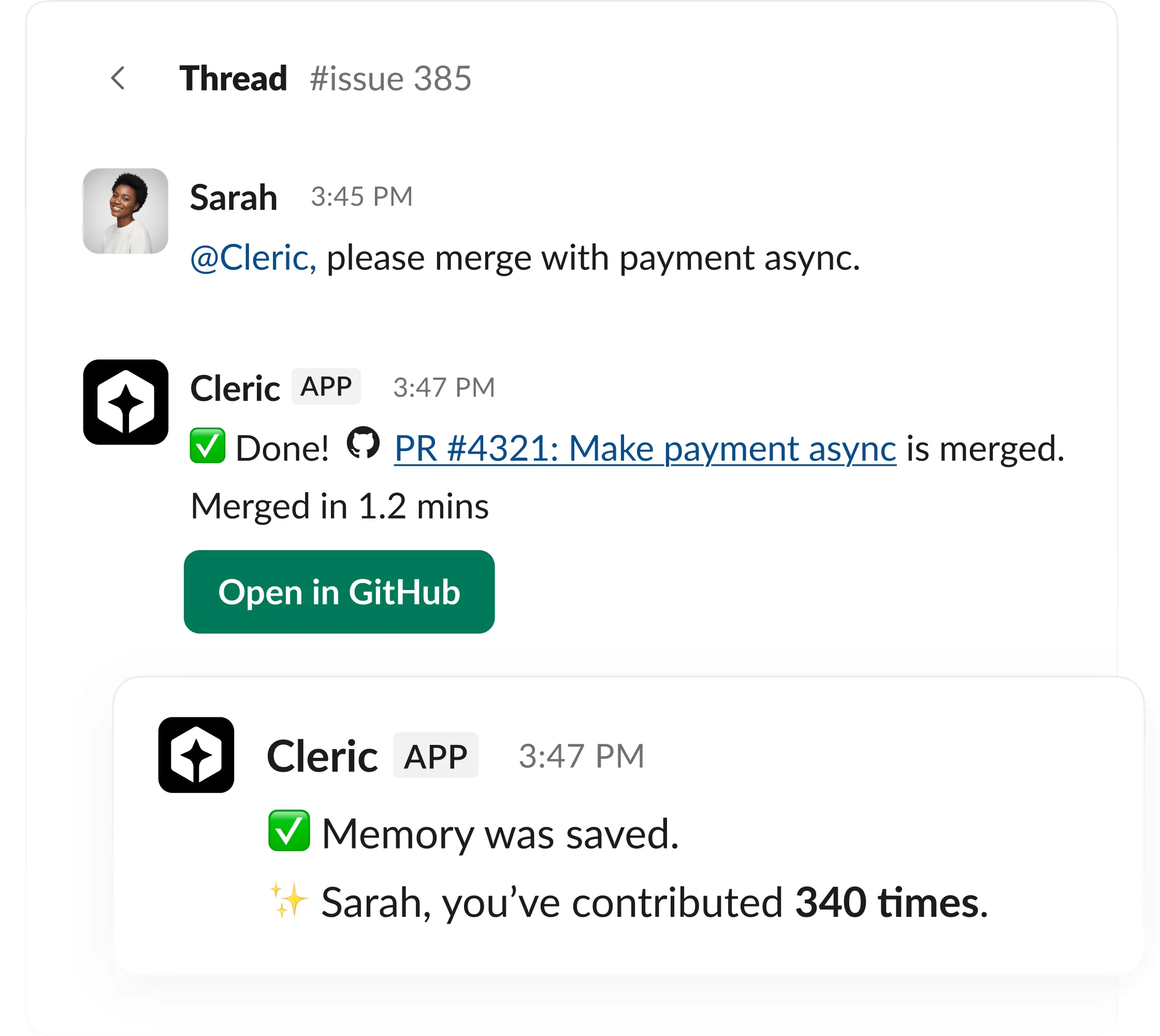
Learns from failure
Engineers leave, context doesn’t. Every resolution becomes institutional knowledge your whole team can use.

Simple on the surface. Serious underneath.
Three purpose-built systems that turn alerts into answers—and make every investigation faster than the last.
Maps your world
Services, dependencies, and ownership mapped automatically. When something breaks, Cleric knows where to look.
Compounds over time
Every fix teaches Cleric something new. Patterns and context accumulate automatically.
Tests every theory
Correlates signals, tests hypotheses in parallel, tracks confidence. Systematic elimination, not guesswork.
Paranoid by design
Read-only by default. Every action logged, every investigation auditable. SOC 2 Type II compliant, with regular manual penetration testing. Your data encrypted everywhere and never used for training.
Built to plug right into your stack
Connect your whole stack in an afternoon. Read access by default, write access when you’re ready.
Unblock your engineers. Start in minutes.
Setup takes minutes. Read-only by default.
